A VPN concentrator is a networking device. It creates secure VPN connections for multiple users at once.
In today’s digital age, online security is crucial. Businesses and individuals need safe ways to connect to the internet. This is where VPN concentrators come in. They offer a centralized solution for managing multiple VPN connections. Imagine having a secure tunnel for your data, protecting it from hackers.
That’s what a VPN concentrator does. It ensures that data between your device and the internet remains private. As cyber threats grow, understanding VPN concentrators becomes vital. They are key tools in maintaining privacy and security online. Let’s dive deeper into how they work and why they are important.

Credit: www.goodaccess.com
Overviews of Contents
ToggleIntroduction To Vpn Concentrators
Understanding network security can be challenging. One important component is the VPN concentrator. A VPN concentrator is a device used in Virtual Private Networks (VPNs). It helps manage multiple VPN connections. This introduction will help explain its role in network security.
Basics Of Vpn Technology
VPNs are essential for secure internet browsing. They create a secure connection between your device and the internet. This connection hides your online activity. It makes your browsing private and safe from hackers.
VPNs use encryption to secure data. Encryption converts your data into a code. Only authorized users can read this code. This ensures that your data stays private and secure.
Want to learn more about VPN? This post could provide more insights. The Best Free VPNs for Torrenting: Secure and Fast Options
Role Of Vpn Concentrators
A VPN concentrator is a crucial part of VPN technology. It handles multiple VPN connections. It is designed to manage large numbers of secure connections. Businesses use VPN concentrators to support remote workers.
The device ensures that each connection is secure. It also manages the data traffic between the connections. This makes the network efficient and secure. VPN concentrators are essential for any organization with many remote users.
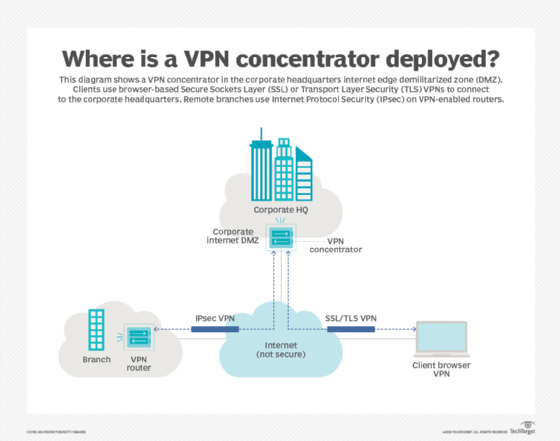
Credit: www.techtarget.com
Key Features Of Vpn Concentrators
VPN concentrators are essential devices that manage multiple VPN connections. They offer several key features that enhance network security and performance. Let’s delve into some of the most important features.
High Availability
High availability ensures that the VPN concentrator is always operational. This feature minimizes downtime and ensures continuous access. It uses redundant hardware and software components. If one component fails, another takes over. This is crucial for businesses that need 24/7 access to their networks.
Scalability
Scalability allows the VPN concentrator to handle increasing workloads. As your business grows, so does the demand on your network. A scalable VPN concentrator can add more users without losing performance. This ensures that your network remains fast and reliable. Scalability is vital for businesses planning for future growth.
| Feature | Benefit |
|---|---|
| High Availability | Ensures continuous network access |
| Scalability | Handles growing workloads efficiently |
By understanding these features, you can choose the right VPN concentrator for your needs. Both high availability and scalability are critical for maintaining a robust and efficient network.
Need to understand more about VPN? This post might help you. Best Vpn for Japan: Unlock Fast, Secure, and Private Browsing
Benefits Of Using Vpn Concentrators
VPN concentrators provide several significant benefits to businesses and individuals. They enhance security, improve performance, and streamline connections for multiple users. Let’s explore these advantages in detail.
Enhanced Security
A VPN concentrator offers robust security features that protect sensitive data. It uses advanced encryption methods to secure the communication between the user and the network. This ensures that any data transmitted is safe from hackers and cyber threats.
- Encryption: VPN concentrators use strong encryption protocols like AES-256.
- Authentication: They offer multi-factor authentication for added security.
- Firewall: Integrated firewalls help block unauthorized access.
Improved Performance
Using a VPN concentrator can significantly improve network performance. It efficiently manages multiple VPN connections, ensuring a smooth and reliable experience for all users.
| Feature | Benefit |
|---|---|
| Load Balancing | Distributes traffic evenly across the network |
| Scalability | Supports a large number of simultaneous connections |
| Bandwidth Management | Optimizes bandwidth usage for better speed |
With these features, businesses can ensure that their network remains fast and efficient, even during peak usage times.
Types Of Vpn Concentrators
Understanding the types of VPN concentrators helps in choosing the right one. VPN concentrators can be categorized into two main types: hardware-based and software-based. Each type has its own advantages and use cases.
Hardware-based
Hardware-based VPN concentrators are physical devices. They are designed for high performance and security. These devices are dedicated to managing VPN connections. They offer robust encryption and can handle many connections at once.
Businesses often use hardware-based VPN concentrators. They provide reliable and secure connections. Because they are physical devices, they do not rely on other systems. This makes them more stable and efficient. But, they can be expensive and require maintenance.
Expand your knowledge about VPN with this article. Private Internet Access Vs Surfshark: Ultimate VPN Comparison
Software-based
Software-based VPN concentrators are applications. They run on existing hardware like servers or computers. These are flexible and easier to deploy. They are cost-effective for smaller setups or businesses.
Many software-based VPN concentrators offer similar features to hardware ones. They provide encryption and manage multiple connections. But, they depend on the performance of the host machine. This can affect their reliability and speed. Software-based solutions are easier to update and scale.
Implementing Vpn Concentrators
VPN concentrators are vital for secure, high-volume network connections. They help in managing multiple VPN tunnels efficiently. Implementing them requires careful planning and execution.
Deployment Steps
Deploying a VPN concentrator involves several steps:
- Assess Requirements: Determine the number of users and required bandwidth.
- Select Hardware: Choose a concentrator that meets your needs.
- Install Software: Install the necessary software on your device.
- Configure Settings: Set up security protocols, such as IPsec or SSL.
- Test Connections: Ensure that all connections are secure and functioning.
- Monitor Performance: Regularly check the performance and make adjustments.
Best Practices
To ensure the optimal performance of your VPN concentrator, follow these best practices:
- Regular Updates: Keep your software and hardware updated.
- Strong Encryption: Use strong encryption methods to protect data.
- Access Control: Implement strict access controls for users.
- Monitor Traffic: Continuously monitor network traffic for anomalies.
- Backup Configurations: Regularly backup your configuration settings.
By following these steps and best practices, you can ensure a secure and efficient VPN concentrator deployment.
Looking for more insights on VPN? You may find this post valuable. Nordvpn Vs Expressvpn: Which VPN Reigns Supreme in 2025?
Challenges And Solutions
Using a VPN concentrator can enhance network security and efficiency. However, it also brings some challenges. Understanding these challenges and knowing their solutions is crucial for smooth operations.
Common Issues
Many organizations face common issues when using VPN concentrators. Below are some of these issues:
- Configuration Errors: Incorrect settings can cause connection problems.
- Performance Bottlenecks: High traffic can lead to slow speeds.
- Security Vulnerabilities: Outdated software can be a risk.
- Scalability Issues: Handling more users can be challenging.
Effective Solutions
There are various effective solutions to address these issues:
- Regular Updates: Keep software up-to-date to avoid vulnerabilities.
- Proper Configuration: Ensure settings are correct to avoid errors.
- Load Balancing: Distribute traffic to prevent bottlenecks.
- Scalability Planning: Plan for future growth to handle more users.
Below is a table summarizing the challenges and their solutions:
| Challenges | Solutions |
|---|---|
| Configuration Errors | Proper Configuration |
| Performance Bottlenecks | Load Balancing |
| Security Vulnerabilities | Regular Updates |
| Scalability Issues | Scalability Planning |

Credit: www.thesecuritybuddy.com
Frequently Asked Questions
What Is A Vpn Concentrator?
A VPN concentrator is a specialized device used in computer networking. It creates secure VPN connections for multiple users. It is essential for managing a large number of VPN tunnels.
How Does A Vpn Concentrator Work?
A VPN concentrator encrypts and decrypts data. It manages multiple VPN connections efficiently. It ensures secure communication over the internet.
Why Use A Vpn Concentrator?
A VPN concentrator provides enhanced security. It is ideal for businesses with many remote employees. It simplifies the management of multiple VPN connections.
What Are The Benefits Of A Vpn Concentrator?
A VPN concentrator offers strong encryption and secure connections. It allows easy management of numerous VPN tunnels. It improves network performance and reliability.
Conclusion
A VPN concentrator is vital for secure, efficient network connections. It ensures data remains private and protected. Using one can simplify managing multiple VPN tunnels. This tool is essential for businesses and individuals alike. With it, you can trust your online activities stay safe.
Consider integrating a VPN concentrator for better security. It’s a smart investment for your digital safety. Stay connected, stay protected.




